User Access Token
User Access Token
It is possible for a JWT application to act on behalf of another user by creating an access token for a specific user instead of the Service Account for the application.
Preconditions
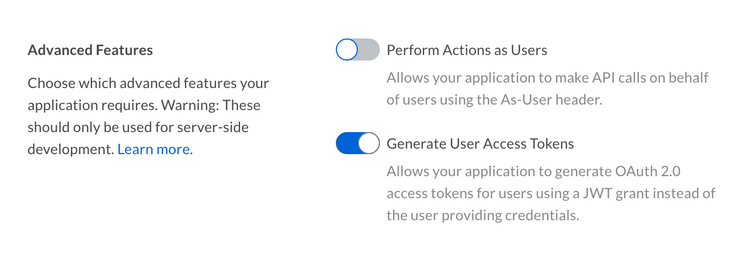
Creating a user access token has a few requirements. Firstly, the application needs to be configured to be allowed to create user access tokens in the developer console.
Additionally, the authenticated user needs to be a user with admin permissions, meaning either an admin, co-admin, or service account. See our guide on User Types for more details.
User Access Tokens with SDKs
To create a Box SDK client that authenticates as a specific user instead of the JWT app's Service Account, follow the same steps as described in the JWT with SDK guide but instead of creating an "Enterprise" client we instead create a user client.
var userId = "12345";
var sdk = new BoxJWTAuth(config);
var token = sdk.UserToken(appUserID);
BoxClient client = boxJWT.UserClient(userToken, userId);
String userId = "12345";
BoxDeveloperEditionAPIConnection api = new BoxDeveloperEditionAPIConnection.getAppUserConnection(userId, config)
user = client.user(user_id='12345')
auth = JWTAuth(
client_id='[CLIENT_ID]',
client_secret='[CLIENT_SECRET]',
user=app_user,
jwt_key_id='[JWT_KEY_ID]',
rsa_private_key_file_sys_path='[CERT.PEM]',
rsa_private_key_passphrase='[PASSPHRASE]'
)
auth.authenticate_user()
user_client = Client(auth)
var sdk = BoxSDK.getPreconfiguredInstance(config);
var client = sdk.getAppAuthClient('user', '12345');
User Access Tokens without SDKs
To create a User Access Token that authenticates as a specific user instead of the JWT app's Service Account follow the same steps as described in the JWT without SDK guide but instead of creating a claim for the enterprise, create one for a specific user ID.
var userId = "12345";
var claims = new List<Claim>{
new Claim("sub", userid),
new Claim("box_sub_type", "user"),
new Claim("jti", jti),
};
String userId = "12345";
JwtClaims claims = new JwtClaims();
claims.setIssuer(config.boxAppSettings.clientID);
claims.setAudience(authenticationUrl);
claims.setSubject(userId);
claims.setClaim("box_sub_type", "user");
claims.setGeneratedJwtId(64);
claims.setExpirationTimeMinutesInTheFuture(0.75f);
user_id = '12345';
claims = {
'iss': config['boxAppSettings']['clientID'],
'sub': user_id,
'box_sub_type': 'user',
'aud': authentication_url,
'jti': secrets.token_hex(64),
'exp': round(time.time()) + 45
}
let user_id = '12345';
let claims = {
iss: config.boxAppSettings.clientID,
sub: user_id,
box_sub_type: "user",
aud: authenticationUrl,
jti: crypto.randomBytes(64).toString("hex"),
exp: Math.floor(Date.now() / 1000) + 45
};
user_id = '12345'
claims = {
iss: config['boxAppSettings']['clientID'],
sub: user_id,
box_sub_type: 'user',
aud: authentication_url,
jti: SecureRandom.hex(64),
exp: Time.now.to_i + 45
}
$userId = '12345';
$claims = [
'iss' => $config->boxAppSettings->clientID,
'sub' => $userId,
'box_sub_type' => 'user',
'aud' => $authenticationUrl,
'jti' => base64_encode(random_bytes(64)),
'exp' => time() + 45,
'kid' => $config->boxAppSettings->appAuth->publicKeyID
];